Elastic Load Balance Helps Enterprises Cope with Heavy Concurrent Traffic
Feb 05, 2021As the mobile Internet grows rapidly, enterprises have to deal with increasingly more scenarios that feature high concurrency. A typical scenario is the shopping festival, during which hundreds of millions of visitors access a website. As a result, servers are overloaded by large numbers of concurrent requests and are slow or even fail to respond to the requests. This greatly affects user experience and may even cause great losses to enterprises.
Elastic Load Balance (ELB) can help enterprises solve this problem.
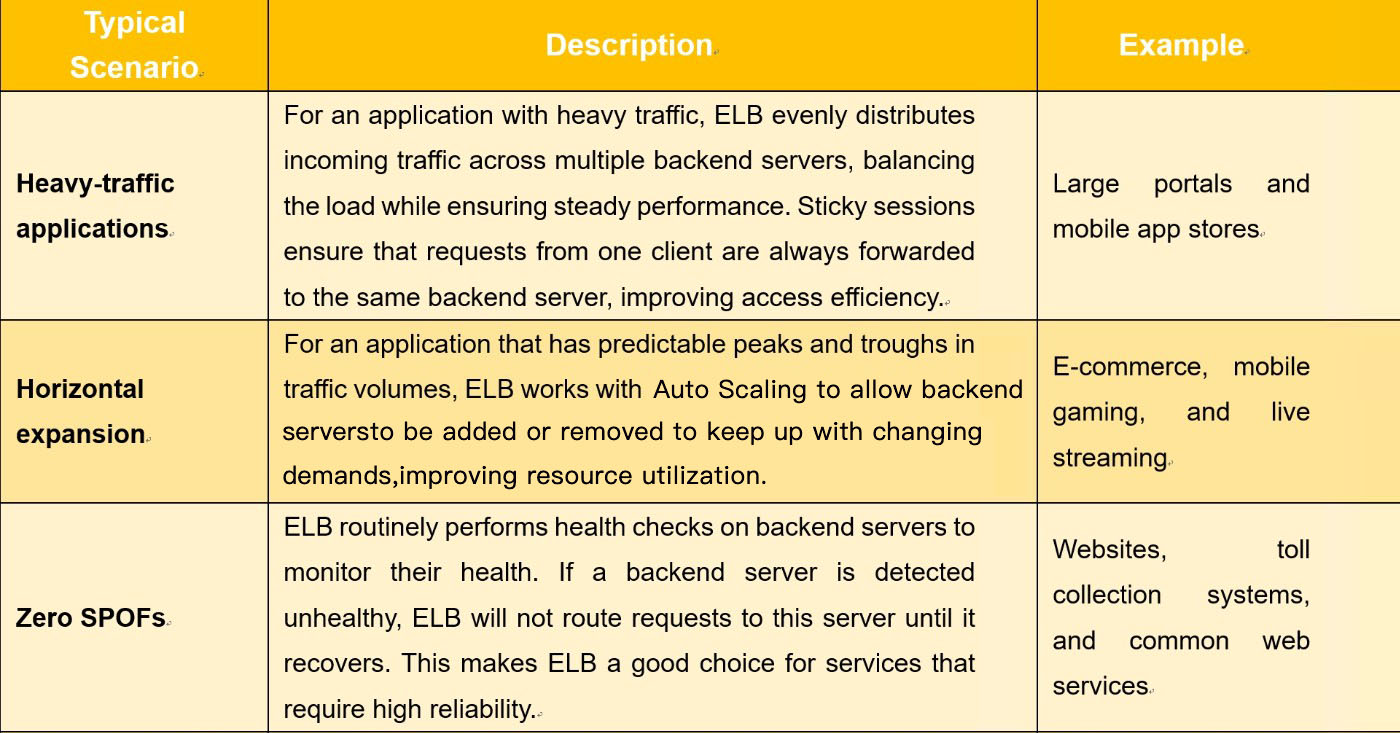
ELB distributes incoming traffic across multiple backend servers and steers requests more efficiently to the correct resources for each end user. ELB improves the availability of applications by expanding their capabilities and eliminating single points of failure (SPOFs). ELB provides load balancing at both Layer 4 and Layer 7 and provides a diverse set of cipher suites to ensure flexibility and security.
ELB has the following advantages:
Robust performance: ELB can establish up to 100 million concurrent connections, meeting your requirements for handling huge numbers of concurrent requests.
High scalability: ELB makes sure that your applications always have enough capacity for varying levels of workloads, and it can work with Auto Scaling to flexibly adjust the number of servers and intelligently distribute incoming traffic across servers.
Ease of use: Diverse set of protocols and algorithms enable you to configure traffic routing policies to suit your needs while keeping deployments simple.
Capabilities to Handle High Concurrency and Ensure High Availability
Comprehensive Functions to Meet Differentiated Requirements
1. Elastic Scaling
After you add backend servers to an Auto Scaling group, Auto Scaling can dynamically adjust the number of backend servers based on traffic and allocate resources on demand.
2. Traffic Scheduling
ELB uses the protocol and port of the listener to check for requests and routes the requests to the backend servers based on the listening rules. ELB supports three load balancing algorithms: weighted round robin, weighted least connections, and source IP hash.
Weighted round robin: Requests are routed to backend servers in sequence based on their weights. Backend servers with higher weights receive proportionately more requests, whereas equal-weighted servers receive the same number of requests.
Weighted least connections: This algorithm is designed based on the least connections algorithm, which makes its load balancing decision based on the number of active connections to each backend server. In addition to the number of connections, each server is assigned a weight based on its capacity. Requests are routed to the server with the lowest connections-to-weight ratio.
Source IP hash: The source IP address of each request is calculated using the consistent hashing algorithm to obtain a unique hash key, and all backend servers are numbered. The generated key allocates the client to a particular server. This allows requests to be routed based on source IP addresses and ensures that the requests from a client are directed to the same server.

3. Health Check
ELB periodically sends requests to backend servers to check their health. If a backend server becomes faulty, ELB automatically stops routing requests to this server until it recovers.
4. Sticky Session
If requests are routed to different backend servers, your access information will be inconsistent among these servers. Sticky sessions can route the requests in a session to the same backend server, maintaining session continuity and consistency. TCP and UDP listeners use source IP addresses to maintain sessions, and HTTP and HTTPS listeners use HTTP cookies and application cookies to maintain sessions.
5. Advanced HTTP/HTTPS Settings
Forwarding policy: forwards requests based on domain names or URLs and applies to scenarios where the status of multiple servers cannot be synchronized.
Mutual authentication: authenticates the identities of both communication parties to ensure security and is suitable for mission-critical services, such as bank payment.
HTTP redirection to HTTPS: routes the requests to access a website over HTTPS to improve security.
Server name indication (SNI): allows a server to present multiple certificates for multiple secure sites on the same IP address.
6. Access Control
ELB allows you to configure a whitelist or blacklist to flexibly control access to a specific listener.

